Supper basic here, but I just wanted to write up some notes on a fun little CTF starter I did.
The description of this challenge said, here is the executable, get a URL and password out of it.
First thing I always run is strings:
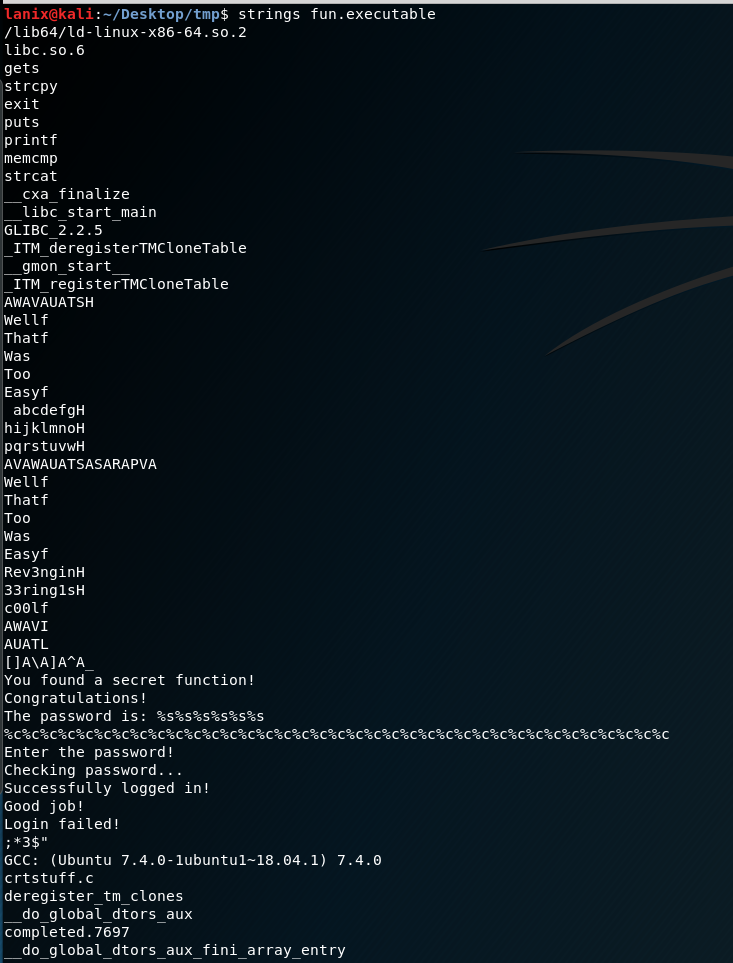
Well…we see there is a “secret” function we need to find, and we see it gives us the password somehow… Now we need to execute this bad boy in a sandbox, I usually create a vm that I can blow away, copy the executable there then run it with some tools. First we will run objdump on it to see what functions are in this bad boy:
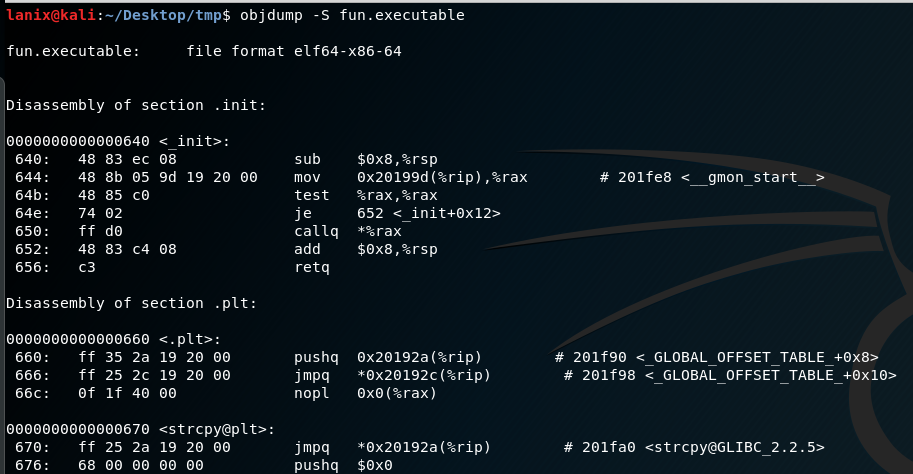
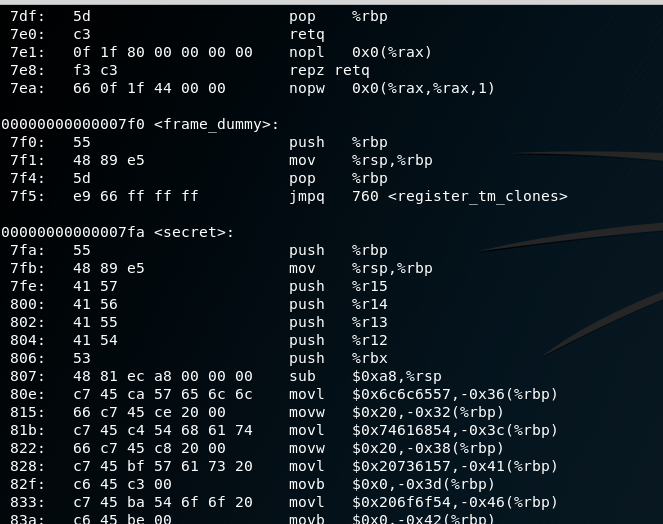
This is where we find the function name…is actually called secret! LOL
Now we decide what way to run this bad boy, do we put it into gdb to debug it or use ltrace? Lets start with ltrace:

Could it be that easy? Lets try the “Well That Was Easy ” (notice the space after the word “Easy “….So we input that into the waiting prompt:
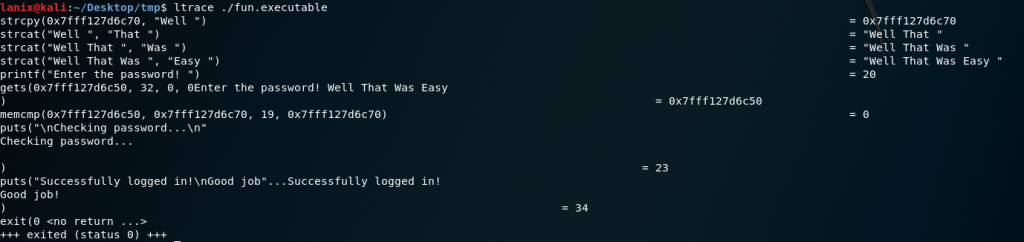
Definitely was the correct password! Now we need to find the URL in this bad boy….so lets move over to the gdb. First we will set a break on main, then try running that hidden function called “secret”:
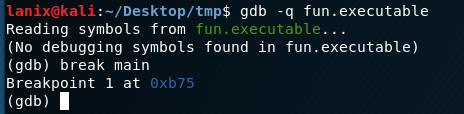
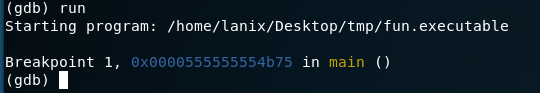
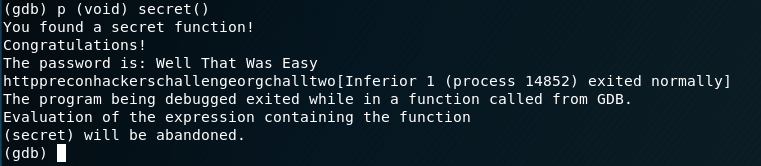
And…there we go, not only do we see the password in this way but we also see the URL we needed!
Lets try a different approach, lets say we didn’t use ltrace and jumped right into the gdb, it wouldn’t be clear about that space after the word “Easy “….So… we could step through the app in this way:
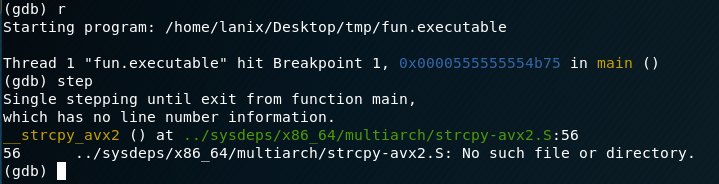
Now after we use the step command gdb will only execute each line of the program as we enter the word “next” or if we use ‘n’ another cheat is if you just hit enter in gdb it will execute the previous command, makes it nice to step through things.
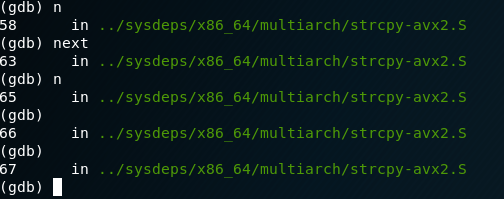
Now that we are stepping into the application (main function) we can check the registers for info:
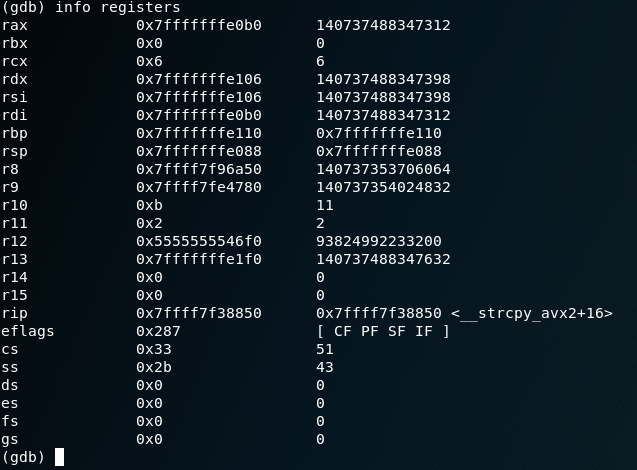
ok, so we see data in several registers, so lets check them out:
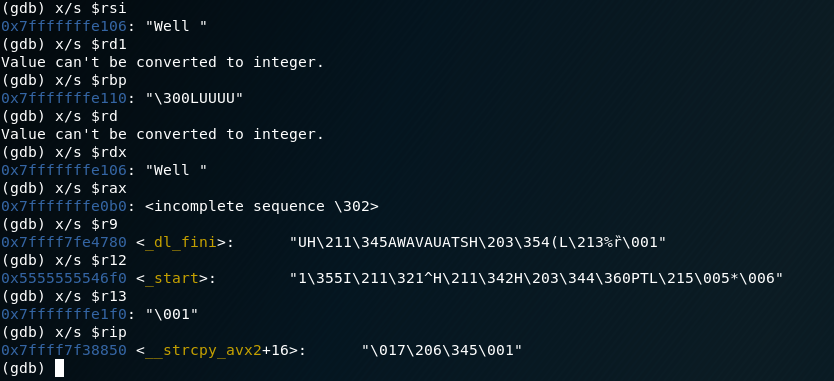
We don’t quite have all we want….so lets keep stepping on…well…you can do that for a while in this case…. so lets just step through the secret function, we first set another break point at the secret function, then step.
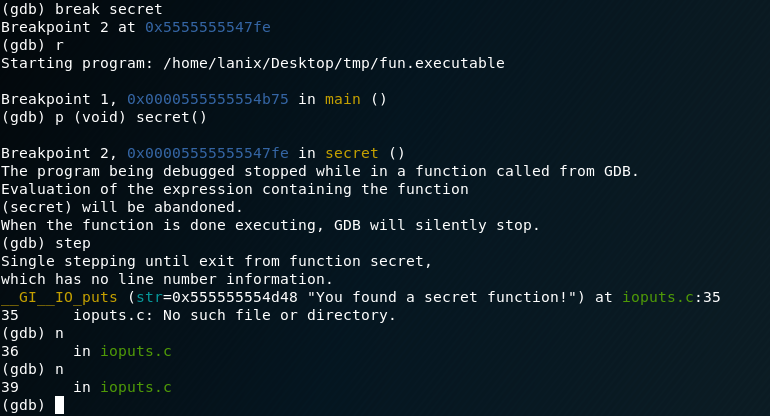
Then start looking at values of registers….and if you do it enough you may find:
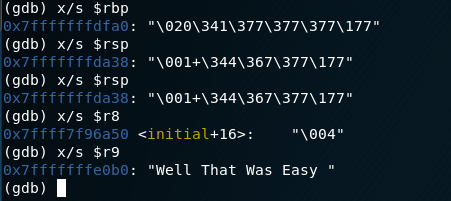
Success! Ok, so now you have the two examples and you can see that in some cases one tool will achieve the objective easier than another….
I hope you liked my little run through here, it is mostly notes for me….and I like to share.